OpenText Network Detection & Response
Defend against threats with real-time network monitoring and response

Robust network threat detection and response
Security teams often struggle with alert fatigue, blind spots in east-west traffic, lack of context for threat triage, and limited visibility into encrypted traffic.
Why OpenText Network Detection & Response?
OpenText Network Detection & Response provides unmatched advantages for your cybersecurity strategy. It delivers complete visibility, lightning-fast detection, and integrated response capabilities to strengthen your security posture with less complexity.
- 100%
complete network threat detection and visibility in one platform
Eliminate network blind spots with SmartPCAP and multi-engine threat detection to monitor encrypted and unencrypted traffic across all environments. - <1 second
threat detection at machine speed
Instantly identify and respond to threats with real-time network monitoring and alerts enriched with context and ready for action. - 3-in-1
detection, forensics, and response combined
Consolidate tools into one scalable solution that simplifies security workflows and boosts SOC efficiency.
Use cases
Equip SOC analysts and security teams to detect, hunt, and respond to threats in real time. From encrypted traffic monitoring to automated incident response, OpenText Network Detection & Response offers proactive threat detection across hybrid environments.
-
Inspect encrypted and unencrypted network traffic using smart sensors to detect threats instantly. Strengthen your threat detection and response posture with real-time network monitoring and response.
-
-
Export threat intelligence to SIEM and SOAR platforms to automate response actions and reduce dwell time. Strengthen your threat detection and response pipeline across the SOC.
-
Protect hybrid networks with sensors and metadata repositories that extend network detection and response coverage to the cloud and beyond, allowing you to scale threat detection and response without adding complexity.
Key features
Transform your network security with powerful capabilities designed to streamline threat detection and response. Implement comprehensive protection while maximizing efficiency and minimizing costs.

Smart sensors
Delivers adaptive threat detection across hybrid networks with scalable, cloud-ready sensors.

Smart PCAP threat context
Links full packet captures to alerts to speed investigations and validate threat response actions.

Unified network instrumentation
Combines forensics, visibility, and detection in one sensor for easy deployment and lower total cost of ownership.

Long-term repository
Retains longer-term, session-based context in data nodes that link high-fidelity network metadata directly to events, regardless of when they occur.

Seamless ecosystem integration
Pushes threat intelligence to SIEM, SOAR, and other systems for streamlined incident response workflows.

Cloud-hybrid deployment
Supports secure operations across on-prem, hybrid, and multi-cloud environments with flexible deployment options.

Downstream visibility
Leverages 360 degree visibility to easily integrate response workflows and improve other tools.
Accelerate the value of OpenText Network Detection & Response
Deployment
OpenText offers a flexible deployment option for OpenText Network Detection & Response.
-
Free up resources, optimize performance, and rapidly address issues
OpenText Off Cloud Managed Services
Professional Services
OpenText Professional Services combines end-to-end solution implementation with comprehensive technology services to help improve systems.
-
Get a trusted partner to guide your information management path
Your journey to success
-
Accelerate the information management journey
Consulting Services
-
Propel your business into the future with modern solutions
NextGen Services
-
Unlock the full potential of your information management solution
Customer Success Services
Partners
OpenText helps customers find the right solution, the right support, and the right outcome.
-
Search OpenText's Partner directory
Find a Partner
-
Explore OpenText's Partner solutions catalog
Application Marketplace
-
Industry-leading organizations that enhance OpenText products and solutions
Strategic Partners
Training
OpenText Learning Services offers comprehensive enablement and learning programs to accelerate knowledge and skills.
-
Meet the demands of all types of users for effective adoption
Learning Services
-
Unlimited access to training with personalized tiers to fit your needs
Learning Subscriptions
Communities
Explore our OpenText communities. Connect with individuals and companies to get insight and support. Get involved in the discussion.
-
Explore ideas, join discussions, and network
OpenText’s forums
Premium Support
Optimize the value of your OpenText solution with dedicated experts who provide mission-critical support for your complex IT environment.
OpenText Network Detection & Response resources
Should you BIY or BUY security?
Read the white paperNatural network threat hunting
Read the white paper7 trends shaping threat detection
Read the white paperWhat to look for in network threat detection and response
Read the white paperShould you BIY or BUY security?
Read the white paperNatural network threat hunting
Read the white paper7 trends shaping threat detection
Read the white paperWhat to look for in network threat detection and response
Read the white paper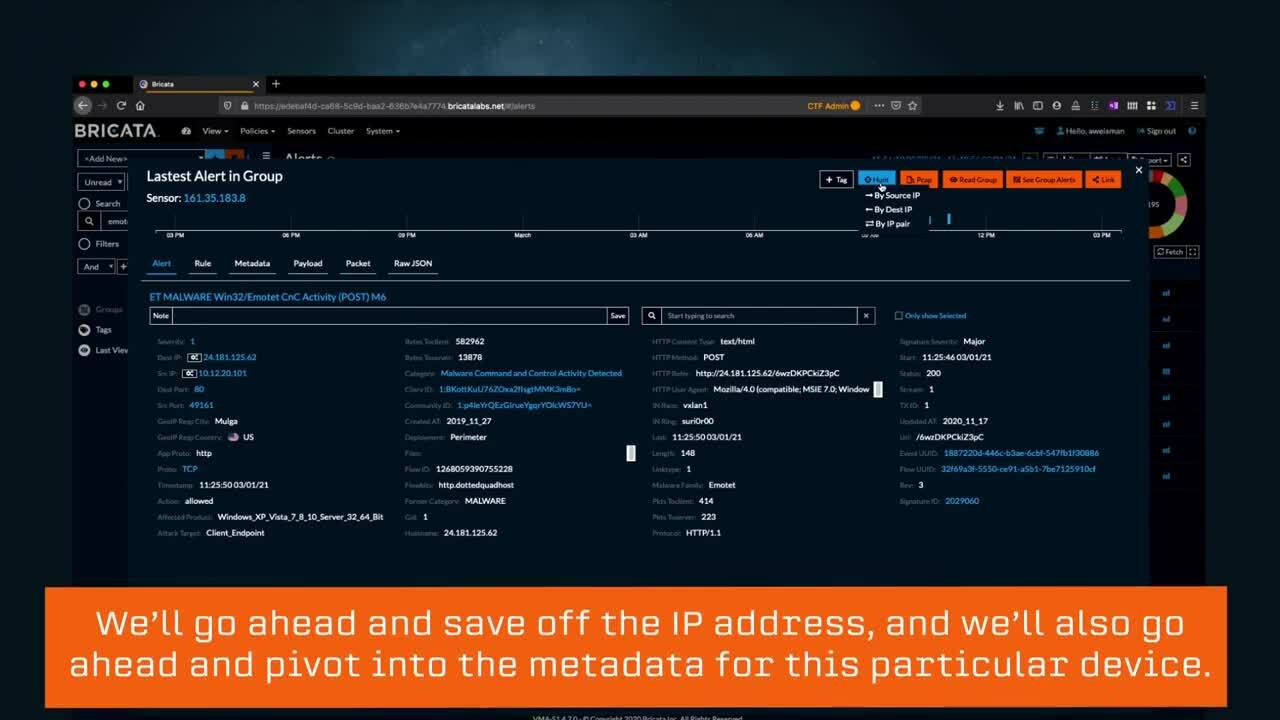
Investigating alerts with OpenText Network Detection & Response
Watch the video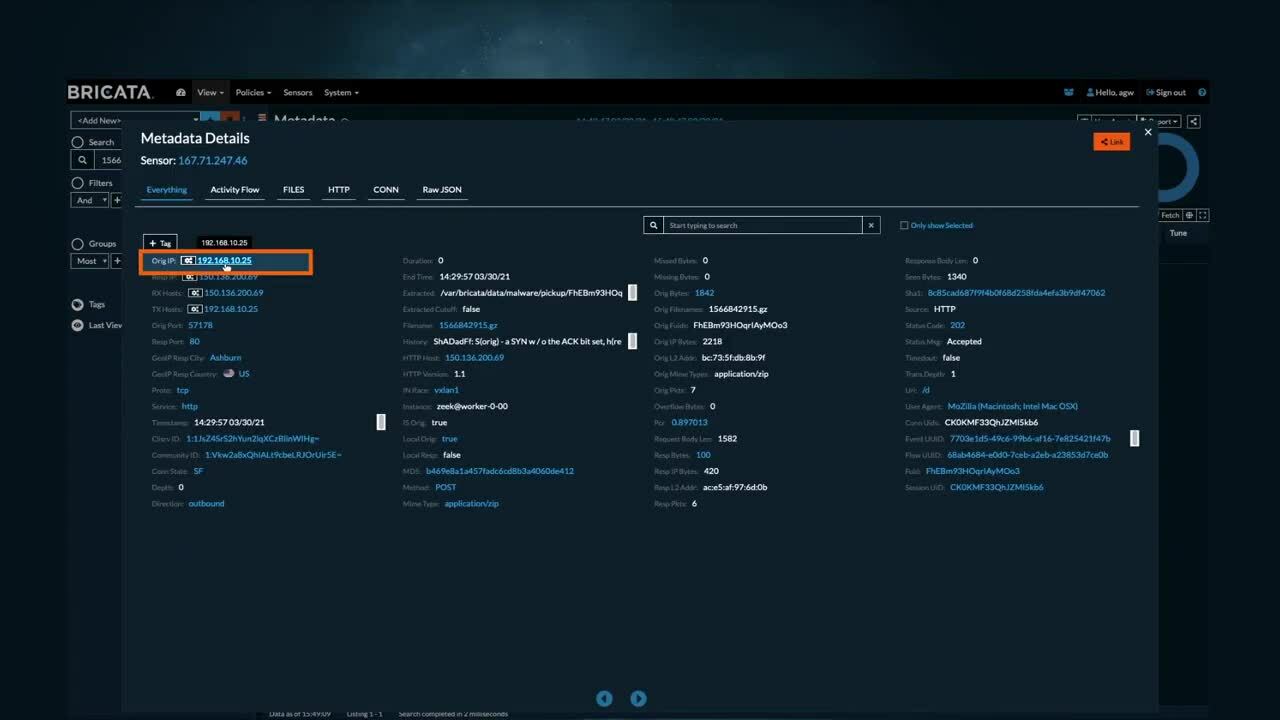
Proactive threat hunting with OpenText Network Detection & Response
Watch the video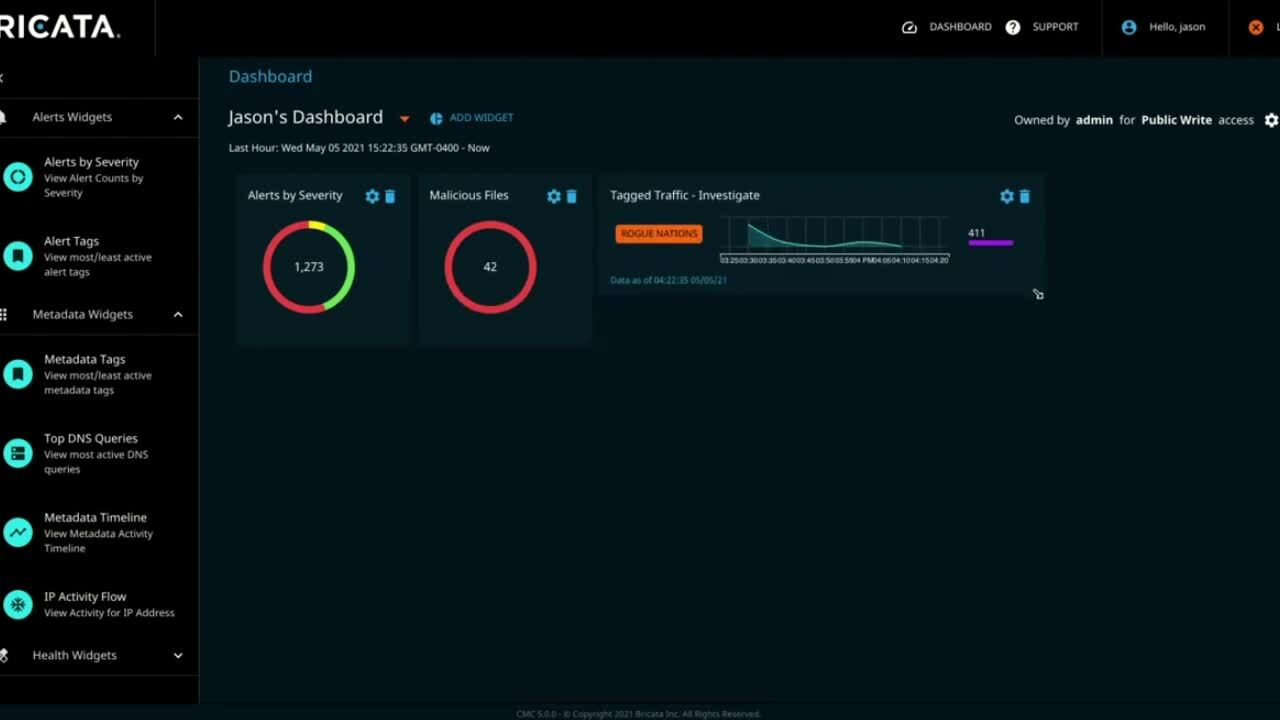
Building effective dashboards with OpenText Network Detection & Response
Watch the video-
OpenText Network Detection and Response analyzes network behavior and traffic patterns to detect lateral movement, command and control activity, and other anomalies missed by signature-based tools like firewalls or antivirus.
-
Yes. OpenText Network Detection and Response uses machine learning and behavioral analysis to correlate signals, suppress noise, and escalate only meaningful, high-fidelity alerts.
-
OpenText Network Detection and Response provides enriched metadata, visual timelines, packet capture, and integration with MITRE ATT&CK to speed up triage and root cause analysis.
-
Yes. OpenText Network Detection and Response offers encrypted traffic analysis using flow data and metadata to identify anomalies without decrypting payloads—maintaining privacy and compliance.
-
OpenText Network Detection and Response offers APIs, syslog, or native integrations to feed alerts and context into tools like Splunk®, QRadar®, Sentinel®, CrowdStrike®, or Palo Alto Networks Cortex®.
-
Baseline modeling starts immediately after deployment, with meaningful detections often within days. Some tuning may be needed for environment-specific behaviors.
-
Unlike conventional tools that may rely solely on signature-based detection, OpenText Network Detection and Response employs multiple detection engines, including anomaly detection and machine learning, to identify both known and unknown threats, reducing false positives and enhancing threat visibility.
-
Yes, it can analyze encrypted traffic by examining metadata and behavioral patterns without decrypting the content, maintaining privacy while detecting anomalies.

Smart PCAP: A time machine for the SOC
With Smart PCAP, you get information that is instant, meaningful, and finely tuned to your needs.
Read the blog
Top 10 network security best practices
To stay ahead of bad actors, follow these 10 best practices to reduce the risk of data compromise.
Read the blog
Take the next step


