OpenText Core Behavioral Signals
Proactively detect insider risks, novel attacks, and advanced persistent threats
Overview

OpenText™ Core Behavioral Signals is an advanced threat-detection tool that uses user entity behavior analytics (UEBA) and 100%-online, unsupervised machine learning (ML) to detect behavioral anomalies across the organization and empower threat hunters. It evolves with the organization so teams can detect insider risk, novel attacks, and advanced persistent threats without needing to maintain rules or update thresholds.
How OpenText Core Behavioral Signals can benefit business
-
Detect difficult-to-find threats
Identify behavior changes and detect adversaries that rule-bound systems struggle to detect, even if attackers change their method of attack.
-
Increase analyst efficacy and efficiency
Transform billions of events into a handful of actionable threat leads, freeing analysts to focus on the threats that matter the most.
-
Automate maintenance and tuning
Gain contextually rich leads with 100%-online, unsupervised ML models that automatically adjust to your organization’s level of normal—without rules or thresholds.
-
Reduce insider attack remediation costs
Catch insider threats in days—not months—to drastically reduce remediation costs.
Why OpenText Core Behavioral Signals?
-
Machine learning foundation
Rely on hundreds of unsupervised machine learning models to detect behavioral anomalies that indicate threats.
-
Adaptive threat detection
Adjust to new normals with advanced threat detection that automatically adapts to your organization with every new event.
-
Simplified threat hunting
Enable analysts to focus their attention on stopping threats with automated ML training and the elimination of rules and thresholds.
Key features
-
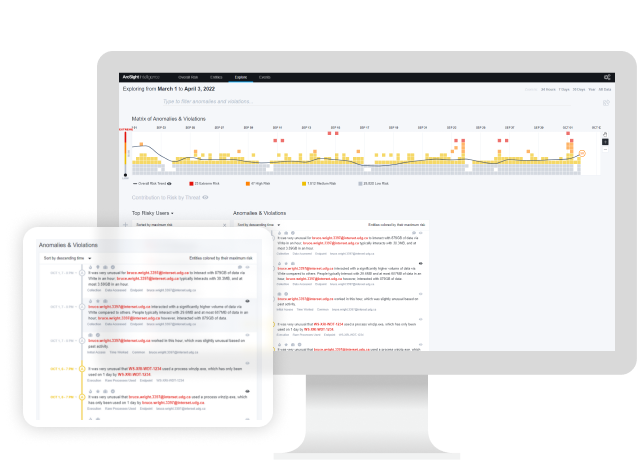
Organizational risk at a glance
Provides dashboards that make it easy to see the overall risk of the entire organization, view trends, highlight individual risks, and quickly address threats.
-
Dynamic anomaly and risk timelines
Presents an entity’s risk profile over time—including the anomalies that contributed to its risk score—and offers advanced filtering so threat hunters can focus in on anomalies of interest.
-
Fully transparent alerts
Accelerates threat hunting with context-rich leads—including visualizations and highly readable descriptions of the anomalies—backed by the events that caused them.
-
Analyst collaboration
Enables real-time collaboration within one centralized location so analysts can quickly identify attacks by leaving comments, applying visual flags, and marking events with user-defined tags.
-
Raw event viewer
Uses a normalization process that retains all raw log fields, enabling users to review the exact details that contribute to an increased risk score.
-
Anomaly mapping
Delivers insights into security stack vulnerabilities by mapping anomalies to MITRE ATT&CK® tactics.
-
API integration
Leverages APIs to integrate with existing SOAR and threat-ticketing systems, allowing users to create tickets or automate actions with ease.
-
Expanded threat hunting capabilities
Supports bundling with OpenText™ Threat Hunting Services to deliver world-class threat analytics with expert, human support.
How to buy
OpenText Core Behavioral Signals
| Organizational risk at a glance |
|---|
| Dynamic anomaly and risk timelines |
| Fully transparent alerts |
| Analyst collaboration |
| MITRE ATT&CK mapping |
| Raw events viewer |
| APIs for SOAR and trouble ticketing system |
| CrowdStrike Falcon data support |
| Public cloud |
|---|
Accelerate the value of OpenText Core Behavioral Signals
Professional Services
OpenText Professional Services combines end-to-end solution implementation with comprehensive technology services to help improve systems.
- Get a trusted partner to guide your information management pathYour journey to success
- Propel your business into the future with modern solutionsNextGen Services
- Accelerate your information management journeyConsulting Services
- Unlock the full potential of your information management solutionCustomer Success Services
Partners
OpenText helps customers find the right solution, the right support, and the right outcome.
- Search OpenText's Partner directory Find a Partner
- Industry-leading organizations that enhance OpenText products and solutionsStrategic Partners
- Explore OpenText's Partner solutions catalogApplication Marketplace
Training
Learning Services offers comprehensive enablement and learning programs to accelerate knowledge and skills.
- Meet the demands of all types of users for effective adoptionLearning Services
- Get expertise as neededFlexible Credits
Communities
Explore our OpenText communities. Connect with individuals and companies to get insight and support. Get involved in the discussion.
- Discover the latest insights in product developmentOpenText technical blogs
- Explore ideas, join discussions, and networkOpenText community
Premium Support
Optimize the value of your OpenText solution with dedicated experts who provide mission-critical support for your complex IT environment.