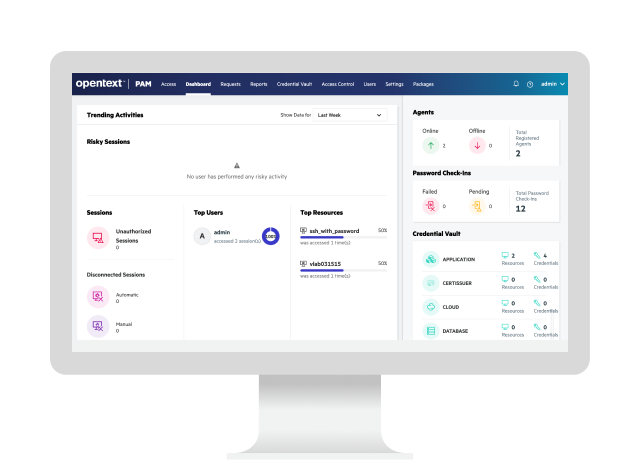
OpenText Privileged Access Manager (NetIQ)
Secure and control privileged access to protect critical assets
KuppingerCole IGA Leadership Compass reportRead the report
Overview
Organizations are collecting and using more data than ever before, increasing breach and regulatory compliance risks. How do you ensure sensitive information is only available to authorized individuals across massive data libraries and distributed staff?

Why OpenText Privileged Access Manager?
OpenText Privileged Access Manager stands out with its holistic approach to privileged access management (PAM), integrating robust security features, advanced automation, and a user-friendly design into a scalable platform.
- Precision
Manage access rights easily with granular control
Fine-tune access through ActiveView to ensure nuanced, role and responsibility-based privileges. - Visibility
Swiftly identify threats and anomalies across the enterprise
Monitor activity through the entire privileged identity lifecycle, enhancing security and compliance. - Automation
Streamline processes to free IT
Built-in workflow automation handles privileged account management so staff can focus on priority projects.
Use cases
Enforce strict access controls, mitigate risk, and meet regulatory requirements efficiently. Ensure visibility into who accesses critical systems and when via comprehensive tools that monitor, manage, and audit privileged user activity.
-
Implement a unified platform for managing privileged access, including advanced controls for monitoring and auditing activities.
-
Track and understand privileged account activities with real-time threat detection, automated alerting, and detailed audit trails.
-
Ensure access is granted based on roles, contexts, and risk levels through granular policy definitions.
-
Automate provisioning, de-provisioning, and credential rotation. Enhance operational efficiency and ensure consistent privilege changes to improve overall management accuracy.
-
Leverage a scalable architecture that integrates seamlessly with existing IT systems to enhance current value while supporting future growth.
-
Implement a user-friendly interface that enables administrators to quickly configure settings, monitor activities, and generate reports. Reduce the learning curve for new users and enhance the efficiency of privilege management tasks.
Key features
Mitigate risks associated with privilege abuse and simplify administration, enhancing overall security and operational efficiency.

Enterprise credential vault
Safeguards credentials with an enterprise-grade vault for enhanced security and access control.

Privileged account monitoring database
Enhances security by monitoring privileged accounts for users, tools, and applications within the database.

Risk profiling for high-risk users
Swiftly identifies high-risk users through advanced risk profiling to implement proactive security measures.

Flexible deployment and support
Deploys seamlessly on Windows and Linux systems with the flexibility of both agent-based and agentless support.
Accelerate the value of OpenText Privileged Access Manager
Professional Services
OpenText Professional Services combines end-to-end solution implementation with comprehensive technology services to help improve systems.
-
Get a trusted partner to guide your information management path
Your journey to success
-
Accelerate your information management journey
Consulting Services
-
Propel your business into the future with modern solutions
NextGen Services
-
Unlock the full potential of your information management solution
Customer Success Services
Partners
OpenText helps customers find the right solution, the right support, and the right outcome.
-
Search OpenText's Partner directory
Find a Partner
-
Explore OpenText's Partner solutions catalog
Application Marketplace
-
Industry-leading organizations that enhance OpenText products and solutions
Strategic Partners
Training
OpenText Learning Services offers comprehensive enablement and learning programs to accelerate knowledge and skills.
-
Meet the demands of all types of users for effective adoption
Learning Services
-
Get expertise as needed
Get expertise as needed
Communities
Explore our OpenText communities. Connect with individuals and companies to get insight and support. Get involved in the discussion.
-
Explore and vote on ideas, participate in the forums, and network with your peers
OpenText Enterprise Cybersecurity Community
-
Expert insights, threat intel, and product updates—built for SMBs
OpenText Cybersecurity SMB Community
Premium Support
Optimize the value of your OpenText solution with dedicated experts who provide mission-critical support for your complex IT environment.
OpenText Privileged Access Manager resources
OpenText Privileged Access Manager
Read the data sheetOpenText Privileged Access Manager
Read the product overviewOpenText Privileged Access Manager
Read the data sheetOpenText Privileged Access Manager
Read the product overview-
Privileged Access Management (PAM) safeguards critical infrastructure by securing and controlling administrative access across hybrid environments. It uses identity-driven security controls to ensure real-time access policies align with dynamic business needs.
-
PAM is crucial for mitigating security risks, enhancing governance, and simplifying compliance. It continuously monitors and intelligently manages privileges to protect critical assets and ensure adherence to industry regulations.
-
Privileged users include IT managers, system/database administrators, auditors, consultants, and C-level executives. These users have greater access due to their roles, skills, or legacy permissions. Managing them closely is essential to prevent security breaches.
-
The platform aids compliance by automating the identification and management of privileged accounts, enforcing least-privilege policies, and providing detailed auditing and reporting capabilities. This approach reduces audit preparation time and ensures adherence to regulatory standards.
-
OpenText Privileged Access Manager centralizes privileged user access management across the IT landscape, enhancing security measures and streamlining compliance processes. It helps safeguard critical assets and adhere to regulatory standards.

Not ready for ITDR? You can still go adaptive
ITDR provides new protection against identity-based attacks but IAM still has advanced protection.
Read the blog
OpenText recognized as a leader in KuppingerCole’s 2024 IGA Leadership Compass
What do secure systems, smooth audits, and good sleep have in common? Resilient identity governance.
Read the blog






