OpenText Data Access Governance (NetIQ)
Identify and secure unstructured data from unauthorized access
KuppingerCole IGA Leadership Compass reportRead the report
Overview
Identify and address malicious and non-malicious threats that can come from unauthorized access to strategic and mission-critical unstructured data.

OpenText™ Data Access Governance (NetIQ) identifies, secures, and protects an organization’s sensitive and high-value unstructured data from unauthorized access. This includes not only personally identifiable information (PII), but an organization’s intellectual property—“crown jewels” that can include sales forecasts in spreadsheets, legal documents saved as word processing files, financial data in a presentation to shareholders, and more.
Why OpenText Data Access Governance?
The OpenText Data Access Governance development team has continuously been addressing the objectives of (what would be eventually defined as) the data access governance (DAG) market for over 20 years.
- Identify
files, permissions, and trends
For enterprise unstructured data so you can determine which files to move or delete, which permissions to adjust, and how fast data is growing.
Meet OpenText™ File Reporter - Automate
file movement and cleanup, permissions remediation, and more
Create policies that enable user role-based access, file migration and cleanup, and permissions to remediate and enforce.
Meet OpenText™ File Dynamics - Demonstrate
compliance with data storage and privacy regulations
Quickly prove that only authorized users have high-value storage access. Conduct access reviews via integration with OpenText™ Identity Governance.
Run file system access reviews
Use cases
OpenText Data Access Governance, an integrated product suite comprised of OpenText File Reporter and OpenText File Dynamics, addresses a broad set of use cases.
-
Identify all users who can access a given folder storing sensitive or confidential files or all network folders that a specific user can access.
-
Establish security policies that automatically remediate access permissions to folders storing sensitive and confidential information in the event those permissions are mistakenly changed.
-
Enable department members or users with specific roles to access network folders or shares storing role-specific files via custom policies.
-
Leverage OpenText File Reporter, which enables OpenText Identity Governance to conduct access reviews on structured data repositories.
Learn more -
Migrate or copy files or folders from one location of the network to another through automated policies.
-
Delete or archive files automatically according to size, file type, age, or when they were last accessed or modified.
Key features
Through identity and automation, OpenText Data Access Governance offers an extensive set of product features that enable organizations to identify, secure, protect, and manage their unstructured data.

On-premises and Microsoft 365 cloud application reporting
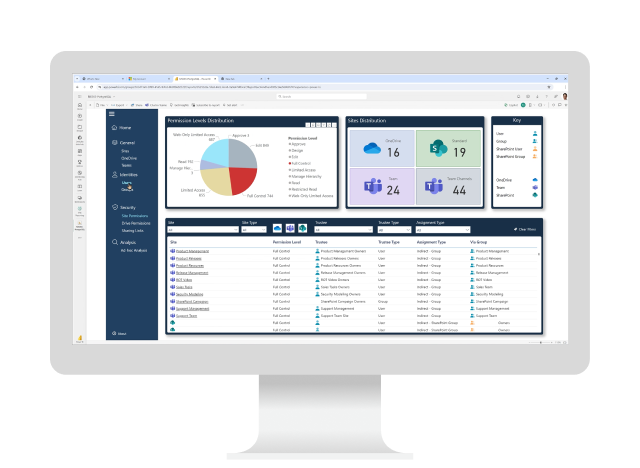
Identifies stored files on-premises or in Microsoft SharePoint Online, Teams, or OneDrive document libraries. Discover their sizes, time of last access, locations of duplicates, and access rights.

Automated security policies
Keep network folders storing confidential files secure through automated policies that can grant or restrict access, notify network admins of changes in permissions, and restore changed permissions.

Active Directory and Entra ID security reporting
Integrates OpenText File Reporter with Microsoft Active Directory and Microsoft Entra ID to report on permissions tied to the Microsoft Windows Server and Microsoft Entra ID file systems.

Flexible reporting and analytics
Enables data insights through built-in reports, Custom Query reports, designed reports, graphical analytics, and even report data exported to third-party tools such as Microsoft Power BI.

Data migration and relocation
Provides multiple methods for automating data migrations via OpenText File Dynamics. These can include all the files and subfolders in a network folder or just a selected set.
Accelerate the value of OpenText Data Access Governance
Partners
OpenText helps customers find the right solution, the right support, and the right outcome.
-
Search OpenText's Partner directory
Find a Partner
-
Explore OpenText's Partner solutions catalog
Application Marketplace
-
Industry-leading organizations that enhance OpenText products and solutions
Strategic Partners
Professional Services
OpenText Professional Services combines end-to-end solution implementation with comprehensive technology services to help improve systems.
-
Get a trusted partner to guide your information management path
Your journey to success
-
Accelerate your information management journey
Consulting Services
-
Propel your business into the future with modern solutions
NextGen Services
-
Unlock the full potential of your information management solution
Customer Success Services
Training
OpenText Learning Services offers comprehensive enablement and learning programs to accelerate knowledge and skills.
-
Meet the demands of all types of users for effective adoption
Learning Services
-
Get expertise as needed
Flexible Credits
Communities
Explore our OpenText communities. Connect with individuals and companies to get insight and support. Get involved in the discussion.
-
Explore and vote on ideas, participate in the forums, and network with your peers
OpenText Enterprise Cybersecurity Community
-
Expert insights, threat intel, and product updates—built for SMBs
OpenText Cybersecurity SMB Community
Premium Support
Optimize the value of your OpenText solution with dedicated experts who provide mission-critical support for your complex IT environment.
OpenText Data Access Governance resources

Automated unstructured data management and secure data access for 20,000 users
Learn more
Gained data visibility and automated data management
Learn moreOpenText Data Access Governance
Read the white paperOpenText Data Access Governance
Read the product overviewOpenText IDM, IG, and DAG solution
Read the solution overviewMitigating risk through identity to govern access to unstructured data
Read the solution overviewOpenText File Reporter
Read the product overviewOpenText File Dynamics
Read the product overviewOpenText Data Access Governance
Read the white paperOpenText Data Access Governance
Read the product overviewOpenText IDM, IG, and DAG solution
Read the solution overviewMitigating risk through identity to govern access to unstructured data
Read the solution overviewOpenText File Reporter
Read the product overviewOpenText File Dynamics
Read the product overview
How to create permissions scan policies in OpenText File Reporter
Watch the video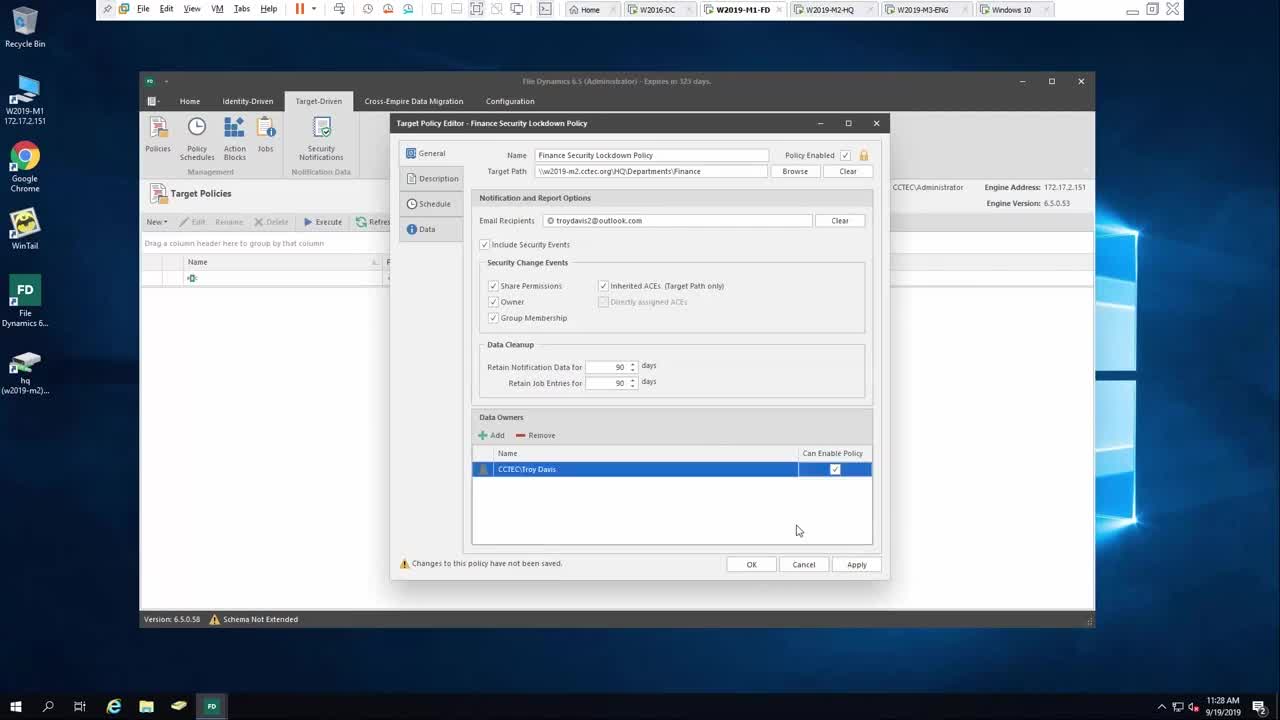
How to create a security lockdown policy with OpenText Data Access Governance
Watch the videoData access governance: The right people, the right access, the right time
Watch the webinarRaising access security without driving users crazy
Watch the webinarData access governance: The right people, the right access, the right time
Watch the webinarRaising access security without driving users crazy
Watch the webinar-
Through reporting and analytics, you can identify which sensitive and high-value data is accessible by unauthorized users—either through improper group membership access or the data being stored in a less secure location—and then implement policies or workloads to take action to remediate the risks.
-
Through target-driven policies that you apply to sensitive and high-value network folders or shares, you can lock down access to only authorized users, monitor unauthorized access attempts, and perform data cleanup actions.
-
OpenText Data Access Governance generates an abstraction that OpenText Identity Governance can utilize to conduct access reviews on unstructured data repositories. This enables you to provide attestation in an audit that only authorized users can access sensitive and high-value unstructured data.
-
As OpenText™ Identity Manager (or any other account provisioning system) provisions network application access to users, OpenText Data Access Governance can simultaneously provision personal network storage for users and provide user role-based access to collaborative storage for teams and projects.
-
OpenText Data Access Governance protects your sensitive and high-value data repositories by limiting access permissions to only those users authorized through policy, preventing “privilege creep” that can occur over time.





